Securing your HTTPS Apache 2.4 web server with correct parameters
Tue-2014-05-06 1 Comment
Warning: Keep in mind this is an ongoing field that is quickly changing. Vulnerabilities in protocols and implementations are discovered daily. If you read this information in a few months or even weeks, things could be radically different.
The last few days I’ve been researching HTTPS connections from Apache 2.4 webservers. This research was sparked by the recent Hearthbleed bug in OpenSSL. I’ve been reading up on vulnerabilities, cipher suites, encryption and hashing methods ever since.
The general move to SSL certificates with a bitlength > 1024bit also fueled this research. Microsoft removed support for 1024bit root CA certificates from their Operating System through a patch in March 2014.
One particular website that has a lot of information is https://www.ssllabs.com. They host a nifty server test tool at https://www.ssllabs.com/ssltest/. When testing our production webservers, we got this very poor result. We got a C for supporting weak cipher suites. We were also not mitgated against the BEAST vulnerability. This was tested after we patched Hearthbleed.
As you can see in the first line, the server had no preference in cipher suite order. Why is this a problem you ask? With modern browsers you always use a newer cipher suite anyway. The point is that external parties (hackers) can force your web server to use an insecure cipher suite to communicate with them.
The most shocking to me was that we, as sysadmins, including me, never really gave much thought to this. The general idea is that you put an SSL certificate on your webserver and it’s secured. As with so many security related product, this assumption is dead wrong. The default ssl_mod settings are optimized for compatibility, not security. With our web servers getting 10 millions+ hits a month and providing privacy sensitive information, there wasn’t much thought needed to see this needed some serious attention.
After some time we came to the following requirements:
- Create a config that is as secure as possible.
- All common browsers should be able to connect to our websites securely. The highly unsafe IE browsers on the Windows XP platform included.
- SSL3 must be supported for older browsers/platforms.
- We must be mitigated against all know attacks, such as BEAST, CRIME, BREACH, Lucky Thirteen, padding attacks, renegotiation, etc.
This appeared to be quite a challenge. In the case of BEAST this deserved some special attention, because mitigating against BEAST is only possible using RC4 cipher suites in TLS1.0 and SSLv3 connections. Unfortunately the research in cracking the RC4 encryption got a serious boost in March 2013.
After days of testing, I came up with the following:
- Use Apache 2.4.7. This version does not allow the key exchange in Diffie-Hellman cipher suites to be less then 2048bit. It will use the bitlength of the SSL certificate but will use no less then 2048bit.
- Use an Apache binary that is compiles against a recent version (1.0.1g) of OpenSSL lib. This will ensure the serving of ECDHE and ECDHE-ECDSA cipher suites.
- Use a 4096bit SSL certificate. This will strengthen the DHE key exchange mechanism.
- Specifically disable SSLv2 even though it is not supported anymore with recent OpenSSL libs.
- Force the cipher suite order in mod_ssl.conf.
- Use a specific, custom ciphers suite to satisfy your specific needs.
- Use mod_socache_shmcb to allow session caching and session resumption.
- Use the Strict-Transport-Security parameter in your Virtual Host config to support HSTS.
Cipher suites are selected on the following criteria in order of importance:
- Prefer ECDHE-ECDSA cipher suites
- Prefer ECDHE cipher suites
- Prefer DHE cipher suites
- Prefer GCM block cipher suites
- Prefer CBC block cipher suites
- Prefer SHA384 hashing
- Prefer SHA256 hashing
- Prefer SHA hashing
- Prefer cipher suites which support Forward Secrecy
- Prefer cipher suites with 256bit encryption
- Prefer cipher suites with 128bit encryption
- Prefer cipher suites with 112bit encryption
As you can see, encryption bit length is only a minor factor in this. Forward Secrecy preference is implicitly done by preferring the ECDHE and DHE cipher suites.
For us, this would result in the ssl_mod config:
SSLSessionCache shmcb:/var/cache/mod_ssl/scache(512000)
SSLSessionCacheTimeout 300
SSLProtocol -SSLv2 ALL
SSLHonorCipherOrder On
SSLCompression Off
SSLCipherSuite EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:DHE-RSA-CAMELLIA256-SHA:DHE-RSA-CAMELLIA128-SHA:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-SEED-SHA:AES256-SHA256:AES128-SHA256:AES128-SHA:DHE-RSA-DES-CBC3-SHA:DES-CBC3-SHA:RC4-SHA:!aNULL:!eNULL:!ADH:!EXP:!LOW:!DES:!MD5:!PSK:!SRP:!DSS
And the httpd config:
<VirtualHost *:443>
Header always set Strict-Transport-Security “max-age=63072000; includeSubDomains”
Alternatively, you can choose not to support CAMELLIA en SEED ciphers with the following parameter:
SSLCipherSuite EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:AES256-SHA256:AES128-SHA256:AES128-SHA:DHE-RSA-DES-CBC3-SHA:DES-CBC3-SHA:RC4-SHA:!aNULL:!eNULL:!ADH:!EXP:!LOW:!DES:!MD5:!PSK:!SRP:!DSS
It’s up for debate if TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (DHE-RSA-DES-CBC3-SHA) and TLS_RSA_WITH_3DES_EDE_CBC_SHA (DES-CBC3-SHA) are still wanted. These create connections with 112bit cipher strength instead of 168bit which you may think. If you require 128bit, leave them out. the DHE-RSA-DES-CBC3-SHA cipher provides Forward Secrecy, so the key to decode one session, cannot be used for another session.
You might want to put TLS_DHE_RSA_WITH_AES_128_CBC_SHA (DHE-RSA-AES128-SHA) before TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA (DHE-RSA-DES-CBC3-SHA), but since it’s included in EDH+aRSA, you’ll have to write it out.
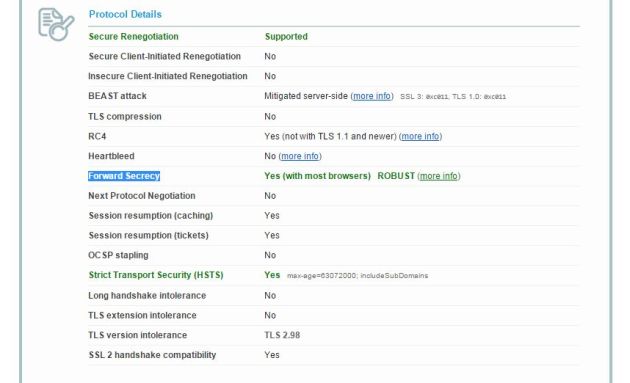
Above settings result in an A+ rated site with BEAST mitigation, Strict Transport Security (HSTS), Forward Secrecy with all common browsers and no RC4 in vulnerable cipher suites:
If you are not interested in mitigating BEAST (as most browsers are patched), you could use the following order:
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:ECDH-ECDSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-SHA384:ECDH-RSA-AES256-GCM-SHA384:ECDH-RSA-AES256-SHA384:ECDH-ECDSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-SHA256:ECDH-RSA-AES128-GCM-SHA256:ECDH-RSA-AES128-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-CAMELLIA256-SHA:DHE-RSA-CAMELLIA128-SHA:DHE-RSA-SEED-SHA:CAMELLIA256-SHA:CAMELLIA128-SHA:DES-CBC3-SHA:!aNULL:!eNULL:!ADH:!EXP:!LOW:!DES:!MD5:!PSK:!SRP:!DSS
Again, CAMELLIA and SEED could be left out:
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:ECDH-ECDSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-SHA384:ECDH-RSA-AES256-GCM-SHA384:ECDH-RSA-AES256-SHA384:ECDH-ECDSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-SHA256:ECDH-RSA-AES128-GCM-SHA256:ECDH-RSA-AES128-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DES-CBC3-SHA:!aNULL:!eNULL:!ADH:!EXP:!LOW:!DES:!MD5:!PSK:!SRP:!DSS
And explicit denial of all RC4 encryption might be preferable:
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:ECDH-ECDSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-SHA384:ECDH-RSA-AES256-GCM-SHA384:ECDH-RSA-AES256-SHA384:ECDH-ECDSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-SHA256:ECDH-RSA-AES128-GCM-SHA256:ECDH-RSA-AES128-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DES-CBC3-SHA:!aNULL:!eNULL:!ADH:!EXP:!LOW:!DES:!MD5:!PSK:!SRP:!DSS:!RC4
I would also advise leaving out the 112bit TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (ECDHE-RSA-DES-CBC3-SHA) cipher suite:
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDH-ECDSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-SHA384:ECDH-RSA-AES256-GCM-SHA384:ECDH-RSA-AES256-SHA384:ECDH-ECDSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-SHA256:ECDH-RSA-AES128-GCM-SHA256:ECDH-RSA-AES128-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DES-CBC3-SHA:!aNULL:!eNULL:!ADH:!EXP:!LOW:!DES:!MD5:!PSK:!SRP:!DSS:!RC4
This would result in all modern browsers/flatforms (IE in Vista and higher, Andriod 4.0.4 and higher, FireFox, Chrome and Safari) to use ECDHE cipher suites with 256bit encryption. The TLS_RSA_WITH_3DES_EDE_CBC_SHA (DES-CBC3-SHA) suite will be used for all exceptions. Also encryption with the potentially vulnerable RC4 cipher is prevented.
References:
“Elliptic curve cryptography” http://en.wikipedia.org/wiki/Elliptic_curve_cryptography
“Elliptic Curve DSA” http://en.wikipedia.org/wiki/Elliptic_Curve_DSA
“Elliptic curve Diffie–Hellman” http://en.wikipedia.org/wiki/ECDHE
“SSL/TLS Deployment Best Practices” https://www.ssllabs.com/projects/best-practices/
“Configuring Apache, Nginx, and OpenSSL for Forward Secrecy” https://community.qualys.com/blogs/securitylabs/2013/08/05/configuring-apache-nginx-and-openssl-for-forward-secrecy
“RC4 in TLS is Broken: Now What?” https://community.qualys.com/blogs/securitylabs/2013/03/19/rc4-in-tls-is-broken-now-what
“Updated SSL/TLS Deployment Best Practices Deprecate RC4” https://community.qualys.com/blogs/securitylabs/2013/09/17/updated-ssltls-deployment-best-practices-deprecate-rc4
“SSL Labs Test for the Heartbleed Attack” https://community.qualys.com/blogs/securitylabs/2014/04/08/ssl-labs-test-for-the-heartbleed-attack
“SSL Labs: Stricter Security Requirements for 2014” https://community.qualys.com/blogs/securitylabs/2014/01/21/ssl-labs-stricter-security-requirements-for-2014
“SPDY” http://en.wikipedia.org/wiki/SPDY
“ChaCha20” http://en.wikipedia.org/wiki/ChaCha20#ChaCha_variant
“Poly1305-AES” http://en.wikipedia.org/wiki/Poly1305
“QUIC” http://en.wikipedia.org/wiki/QUIC
Session Resumption http://en.wikipedia.org/wiki/Transport_Layer_Security#Session_IDs
“HTTP Strict Transport Security” http://en.wikipedia.org/wiki/HTTP_Strict_Transport_Security
“Nginx” http://en.wikipedia.org/wiki/Nginx
“Strong SSL Security on Apache2” https://raymii.org/s/tutorials/Strong_SSL_Security_On_Apache2.html
“Increasing DHE strength on Apache 2.4.x” http://blog.ivanristic.com/2013/08/increasing-dhe-strength-on-apache.html
“OpenSSL cipher suites” https://www.openssl.org/docs/apps/ciphers.html
https://www.ssllabs.com/ssltest/analyze.html?d=payload.hu. This site runs Apache. It’s cipher suites are: “EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS”.
https://www.ssllabs.com/ssltest/analyze.html?d=icnseo.com This server runs nginx. It’s cipher suites are: ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:HIGH:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!CBC:!EDH:!kEDH:!PSK:!SRP:!kECDH;
https://www.ssllabs.com/ssltest/analyze.html?d=blck.io. This site uses mod_spdy voor Apache 2.4.
https://github.com/eousphoros/mod-spdy mod_spdy.
chrome://net-internals/#spdy Monitor SPDY connections in the Chrome browser